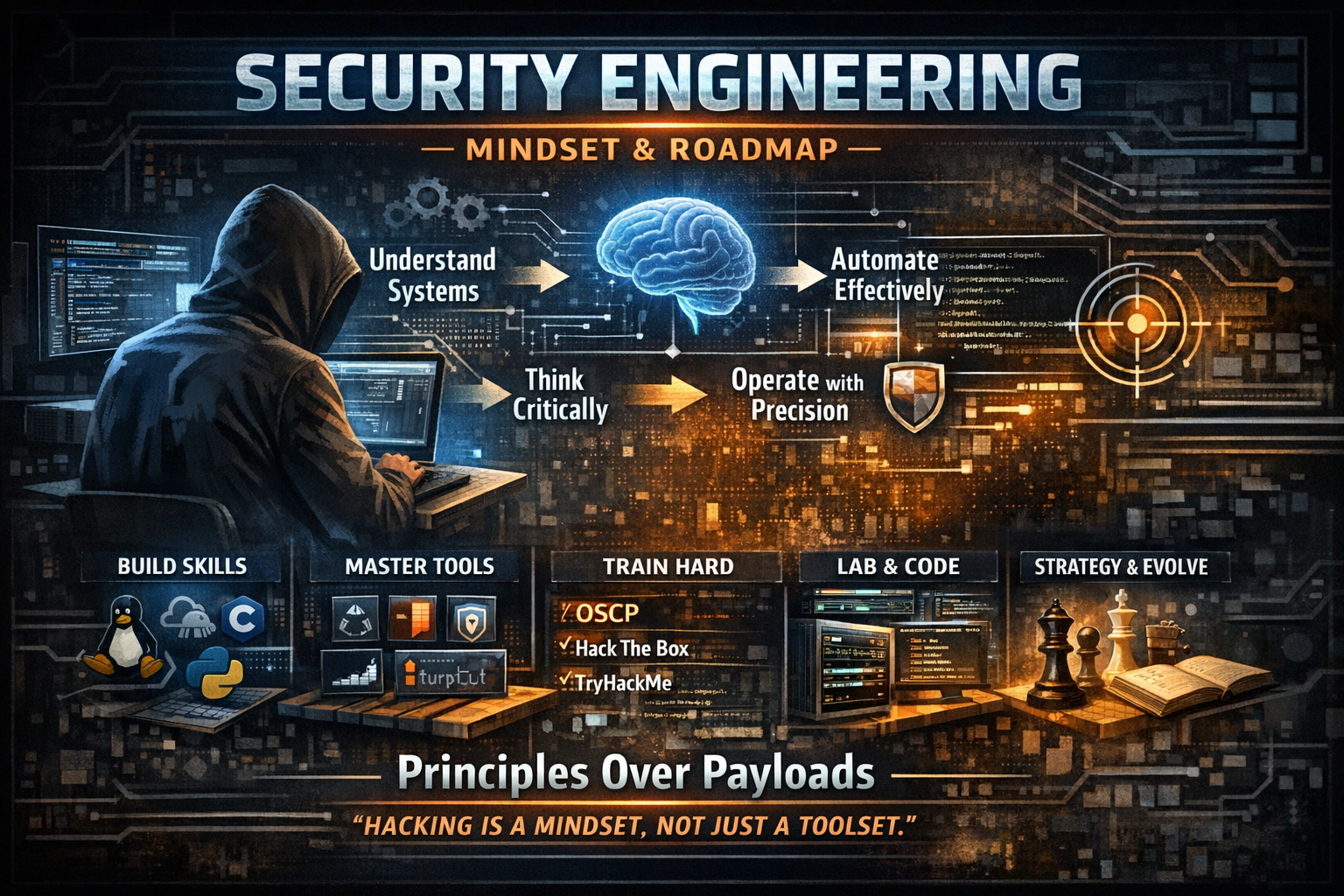
Security Engineering: Mindset, Skills, and Roadmap
A practitioner's framework for developing offensive security expertise through systematic thinking, architectural understanding, and disciplined methodology.

A practitioner's framework for developing offensive security expertise through systematic thinking, architectural understanding, and disciplined methodology.
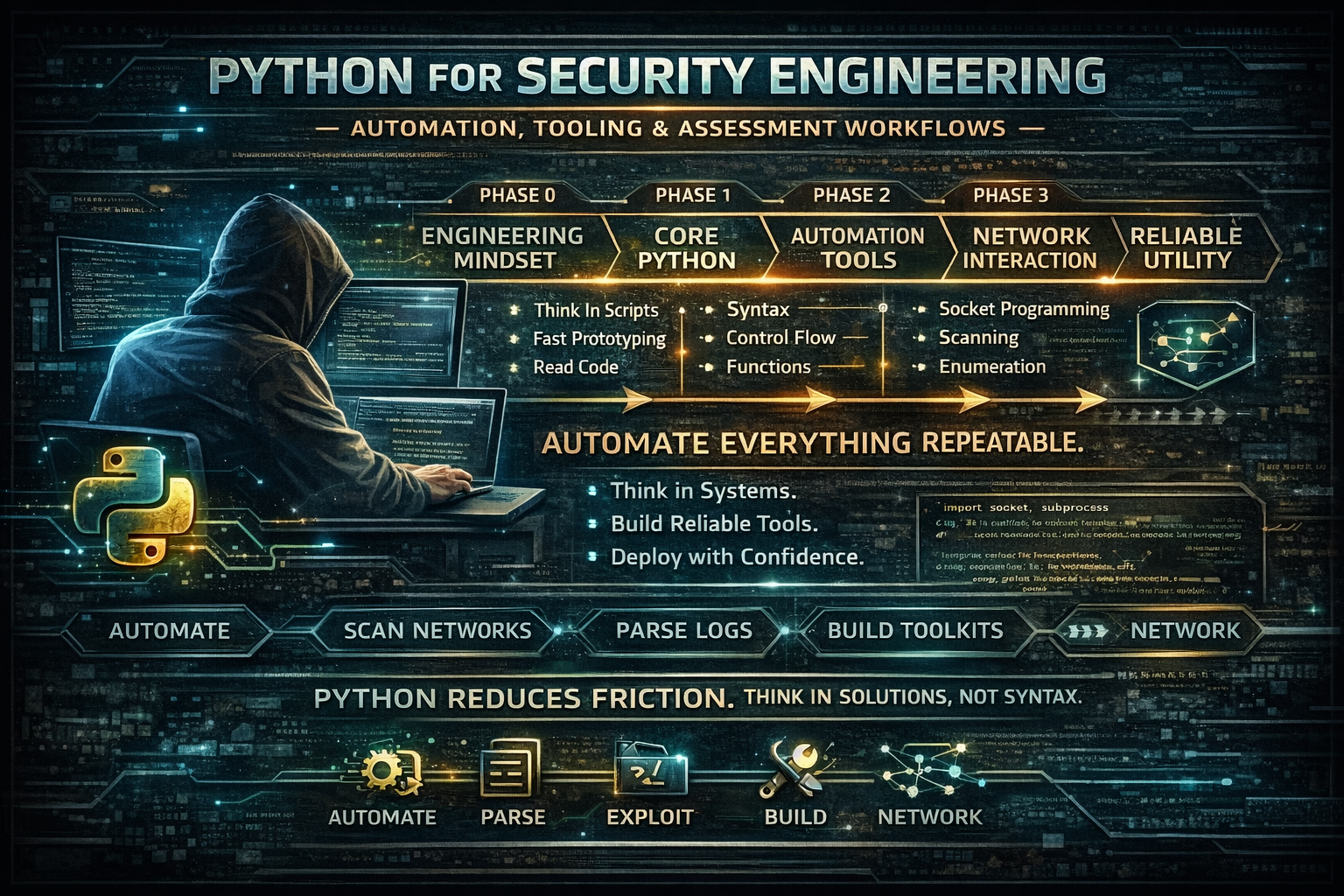
A practical, engineering-focused guide to using Python for security assessments, automation, and internal tooling. Covers scripting fundamentals, network interaction, data handling, and building reliable utilities for real-world engagements.

A curated reference of platforms, datasets, and tools used during security assessments, threat research, and infrastructure analysis. Organized by workflow with practical context.

A practical methodology for leveraging search engines during security assessments. Covers operators, query construction, and techniques for identifying exposed assets, sensitive files, and misconfigurations across internet-facing infrastructure.

A practical approach to building portable, reproducible, and isolated security testing environments using Docker. Suitable for research, professional assessments, and controlled lab work.

A structured and repeatable workflow for assessing modern web applications. Focused on attack surface mapping, business logic validation, and controlled exploitation rather than tool-driven scanning.

A structured and practical methodology for evaluating the security posture of modern wireless networks, focusing on credential exposure, segmentation, rogue infrastructure testing, and defensive validation.
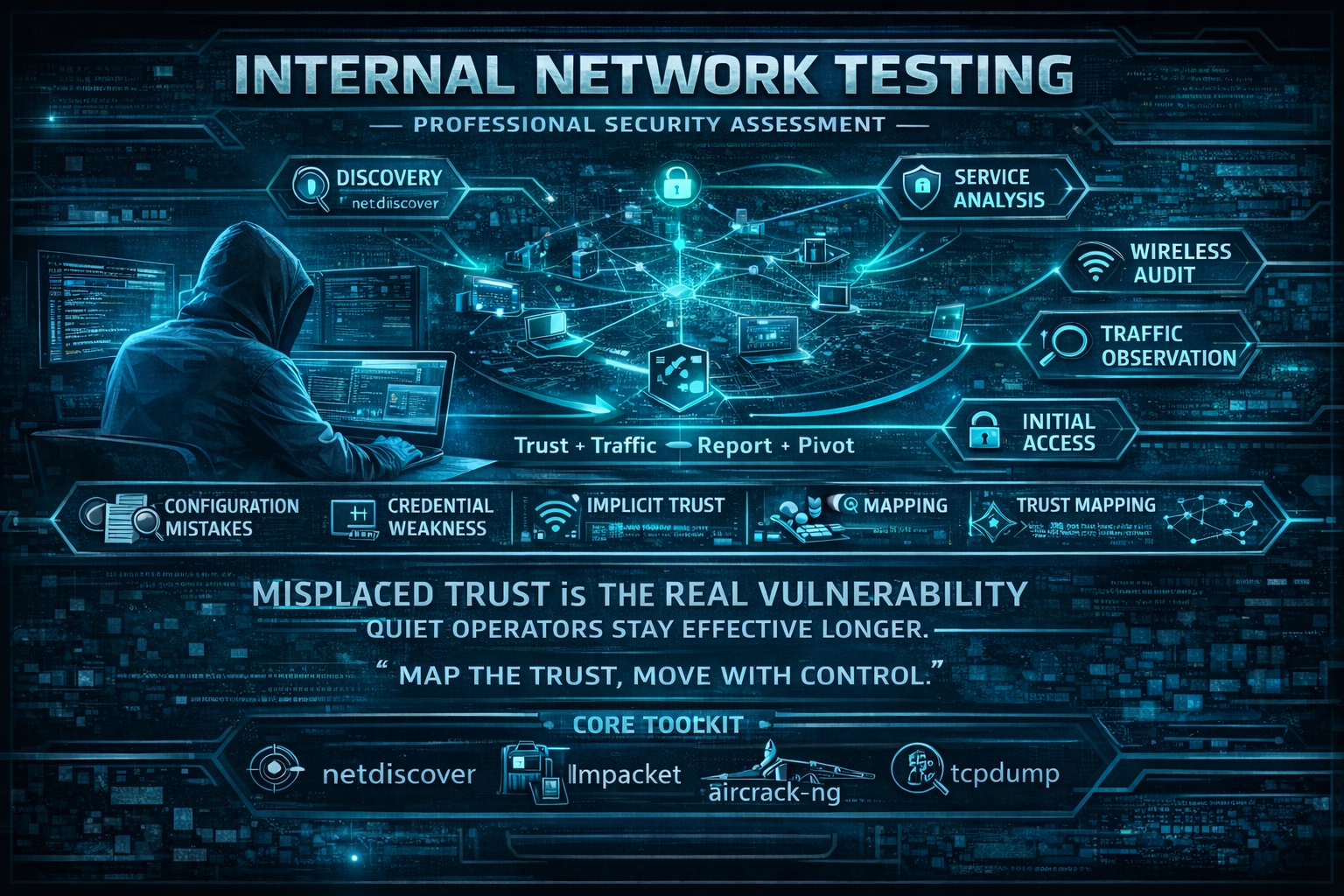
A structured, professional workflow for conducting internal and wireless network security assessments. Focused on enumeration, trust relationships, and controlled lateral movement.